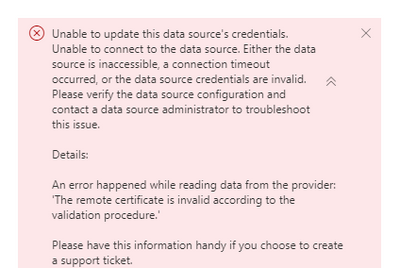
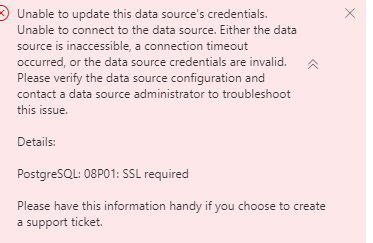
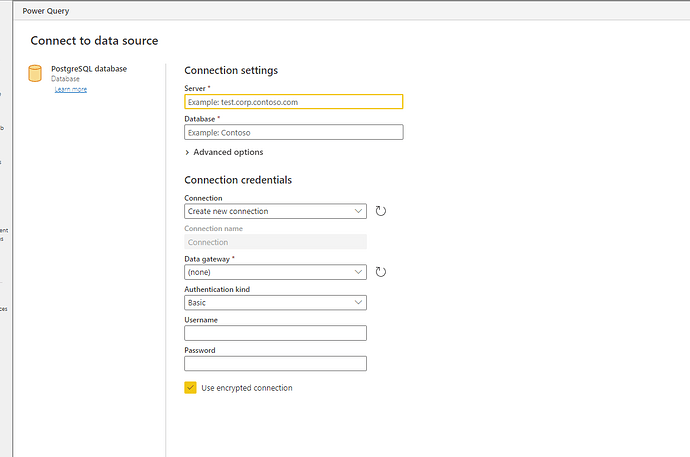
Hey. We have been facing this very issue for years. Finally got a solution a few days back. There’s just not enough information available on the web at all for this. Posting this for anyone who will need it.
This process works both on PowerBI Desktop as well as a cloud datasource on PowerBI Service. There is NO NEED for a gateway required with this!
I am putting an entire step-by-step process here right from spinning up an EC2 Ubuntu machine to getting a certificate that PowerBI service accepts.
- Start a new EC2 instance with Ubuntu 22.04 installed. I started a t3a.nano instance. 8 GB SSD GP3 storage.
Allocate and associate an Elastic IP and point it to the domain yourdb.domain.com .
- Create a new security group for PostgresDB. Open HTTP and HTTPS ports for anywhere access which is required for requesting the SSL certificate.
Open Postgres port 5432 to allow remote access to Postgres.
- Install Postgres using following commands:
sudo apt update
sudo apt install postgresql postgresql-contrib
- Change password of user ‘postgres’ using the following commands:
sudo -i -u postgres
psql
ALTER USER postgres WITH PASSWORD ‘’;
- Create Database with follwing command:
CREATE DATABASE “”;
- Install Certbot on the server to get free letsencrypt ssl certificate using the following command:
sudo snap install --classic certbot
- Generate Certbot certificate using the following command:
sudo certbot certonly --standalone -d yourdb.domain.com
- Add the following line to /etc/postgresql/14/main/pg_hba.conf :
hostssl all all 0.0.0.0/0 md5
- Change listen_address = ‘*’ in /etc/postgresql/14/main/postgresql.conf to allow remote access
Make the following changes as well:
ssl = on
ssl_cert_file = ‘/etc/postgresql/14/main/fullchain.pem’
ssl_key_file = ‘/etc/postgresql/14/main/privkey.pem’
- Run the following commands to copy letsencrypt certificates from its folder to the postgres folder and allow access. Restart postgres.
sudo cp /etc/letsencrypt/live/yourdb.domain.com/fullchain.pem /etc/postgresql/14/main/fullchain.pem
sudo cp /etc/letsencrypt/live/yourdb.domain.com/privkey.pem /etc/postgresql/14/main/privkey.pem
sudo chmod 600 /etc/postgresql/14/main/fullchain.pem /etc/postgresql/14/main/privkey.pem
sudo chown postgres:postgres /etc/postgresql/14/main/fullchain.pem /etc/postgresql/14/main/privkey.pem
sudo systemctl restart postgresql
- The letsencrypt certificate has to be renewed using cron since it expires every three months. For this a bash script ‘renew-certificate.sh’ has been written using the above point 10 in the directory /home/ubuntu/renew-certificate. The file can be made executable chmod +x renew-certificate.sh
Following is the bash script:
sudo certbot renew --post-hook "sudo cp /etc/letsencrypt/live/yourdb.domain.com/fullchain.pem /etc/postgresql/14/main/fullchain.pem &&
sudo cp /etc/letsencrypt/live/yourdb.domain.com/privkey.pem /etc/postgresql/14/main/privkey.pem &&
sudo chmod 600 /etc/postgresql/14/main/fullchain.pem /etc/postgresql/14/main/privkey.pem &&
sudo chown postgres:postgres /etc/postgresql/14/main/fullchain.pem /etc/postgresql/14/main/privkey.pem && systemctl restart postgresql"
- Set the following is the cronjob using the command crontab -e:
0 0 1 * * /home/ubuntu/renew-certificate/renew-certificate.sh